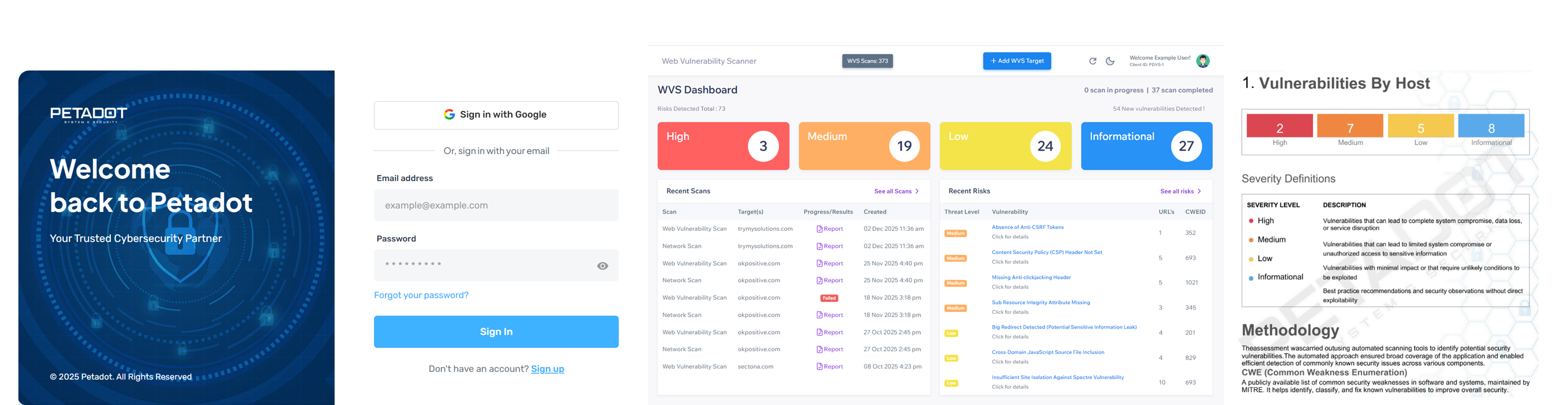
What We Do
Petadot’s Web Vulnerability Scanner (WVS) helps businesses detect & fix security loopholes in websites and web applications before cybercriminals can exploit them. Our scanning is backed by OWASP Top 10 standards for maximum reliability.Our interactive dashboard gives you a complete view of your risk posture from detection to remediation.